RSA is the world’s largest cybersecurity conference and a key moment for the industry, which our product team has eagerly been working towards.
Today we are excited to announce more than 15 new product capabilities for Microsoft Cloud App Security (MCAS).
They are oriented around 4 major themes, as we continue to deliver a unique Cloud Access Security Broker (CASB) that is designed with security professionals in mind and continues to push industry boundaries by providing cutting edge capabilities, simplicity of deployment, centralized management, and innovative automation capabilities.
State-of-the-art Threat Protection
Malware poses risks to organizations and individuals in the form of impaired usability, data loss, intellectual property theft, and monetary loss. Microsoft uses a broad array of tools and techniques to identify, block, and eradicate malware infections wherever they are found.1 As cloud threats continue to evolve, it is becoming increasingly important to detect not only known, but especially zero-day, malware that is infiltrating your cloud environments.
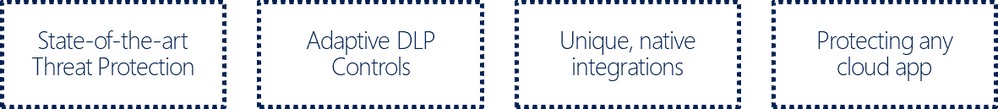
UBA enhancements and User Investigation Priority
By integrating with the Microsoft Intelligent Security Graph, MCAS has an unparalleled view into the evolving threat landscape, enabling us to continuously evolve our detections and enhance our UBA capabilities. At the same time, we recognize that prioritization is key for often understaffed SOC teams. That’s why we have added a new, powerful investigation priority for users, based on the new user analytics engine. It provides admins with an overview of the users who likely pose the greatest risk to the organization and are recommended for immediate review. It takes into consideration several conditions such as the type of alerts, as well as a user’s overall impact to the organization, e.g. their level of access to sensitive information, based on patented UBA mechanisms.
Malware Detonation
Microsoft Cloud App Security is introducing malware detonation capabilities for our API-connected cloud storage apps. Intelligent heuristics allow us to identify potentially malicious files, rather than needing to detonate all files, to minimize the impact on user productivity. Once a suspicious file has been identified, it is then detonated in a sandbox environment and alerts the admins. Malware investigation and detonation is automatically applied to newly uploaded files in near-real time, as well files that already exist in your connected cloud apps.
Adaptive DLP Controls
Hackers want information. Consequently, organizations invest heavily in ensuring their most valuable assets stay protected by making sure they know where and how data travels in the cloud, and that it can only be accessed by authorized users.
We’ve added support for powerful use-cases in Microsoft Cloud App Security for real-time monitoring and control, which now allow you to monitor and control the following situations:
- Apply custom permissions on download - Creating a company-wide labelling strategy is often an extensive task, because permissions must be scoped beforehand to create the labels relevant for your organization. But today’s world organizations provide increasingly flexible work environments for employees, while also collaborating with external parties, creating many conditions to take into consideration. This often makes it difficult to ensure that sensitive data can is protected, but productivity remains high. In Microsoft Cloud App Security we have added a more generic way to protect files in zero-trust situations. It allows organizations to define risky conditions beforehand, such as unmanaged device or external user, and then automatically apply permissions, such as read-only, to the documents upon download from your cloud apps. This provides a much greater level of flexibility and the ability to protect information outside of the pre-configured corporate labels.
- File uploads in any app – enabling scenarios such as preventing uploads of known malware extensions, as well as preventing users from uploading unlabeled files to any corporate app and educating them in the session to add a label to the file to enable the upload.
- Cut/copy and paste in any app– rounding out our robust controls of data exfiltration that already include controlling download and print capabilities, and custom activities such as share.
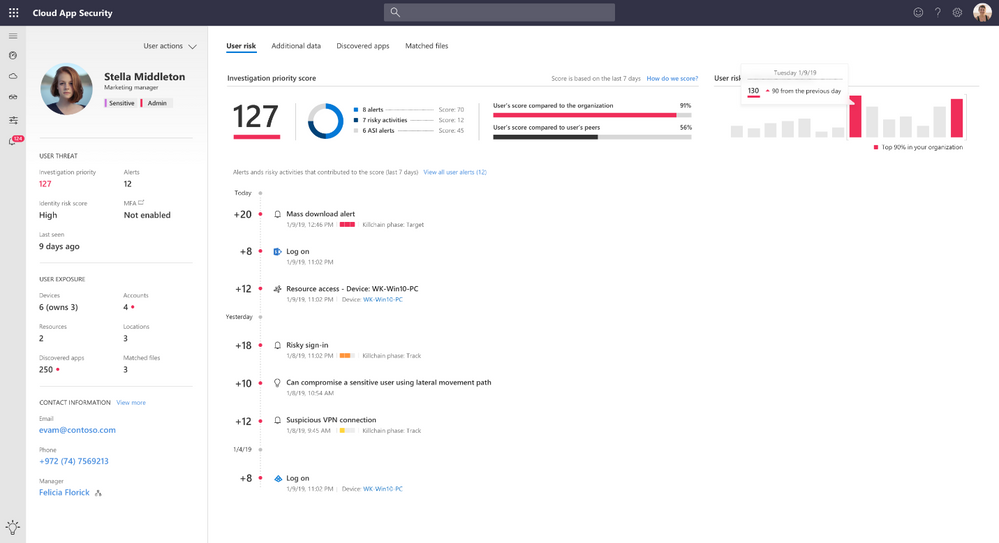
- Sending messages with sensitive content - ensuring that PII data, such as passwords, are not shared in popular collaboration tools such as Slack, Salesforce, and Workplace by Facebook via IM messages, posts or comments. We will also be adding Microsoft Teams shortly.
- Applying download permissions to specific folders in OneDrive for Business and SharePoint Online – We understand that not all folders in OneDrive for Business and SharePoint are the same. Some contain highly confidential data and therefore need a different level of control. This new level of granularity now allows you to ensure your most sensitive data cannot be exfiltrated and you can create policies that work for you.
- Out-of-the-box templates - Session Policies now include built-in templates, such as blocking download of sensitive files, to enable your organization to effortlessly enable popular use-cases around real-time monitoring and control of your sanctioned apps.
Unique, native integrations
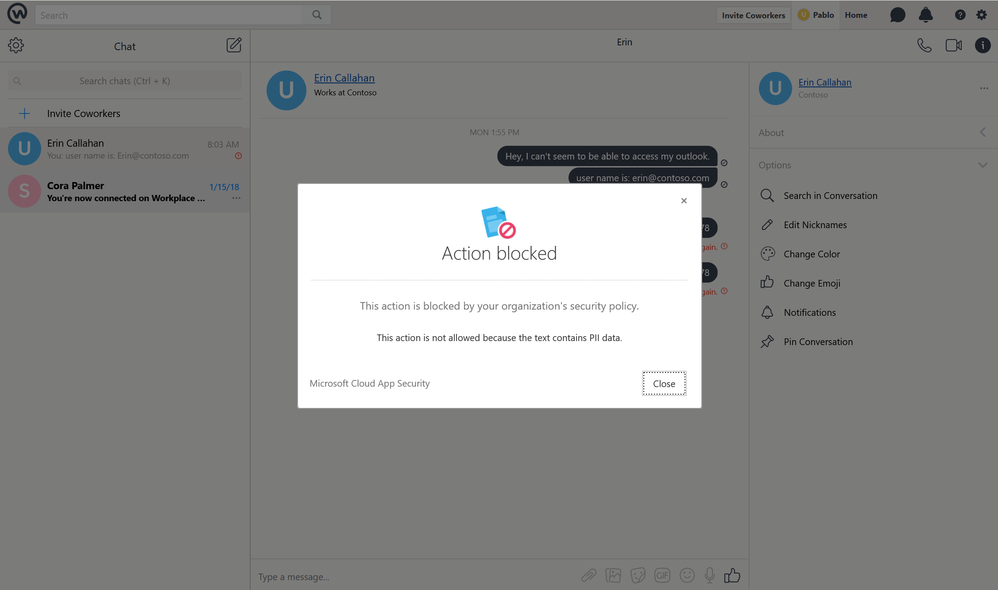
Microsoft Cloud App Security natively integrates with leading Microsoft solutions and we continue to build on this strategy to leverage powerful capabilities from Microsoft’s solution portfolio as part of our CASB, to create unique capabilities.
Last week Microsoft announced its entry into the SIEM market with Microsoft Azure Sentinel, which allows you to aggregate all security data with built-in connectors, native integration of Microsoft signals, and support for industry standard log formats like common event format and syslog.
Microsoft Cloud App Security now integrates with Azure Sentinel and Power BI to leverage security logs in new, powerful ways - allowing organizations to define custom retention times, correlate MCAS Cloud Discovery data with your own data sources, and providing new, powerful ways to visualize the data in custom Power BI dashboards.
Longer, custom retention of Cloud Discovery data
While MCAS has a strict data retention policy and only keeps Cloud Discovery data for 90 days, by integrating with Azure Sentinel, organizations can now leverage their Discovery data within Azure Sentinel to define custom, longer retention times.
This gives admins more flexibility to run queries and visualize data over time directly within Azure Sentinel.
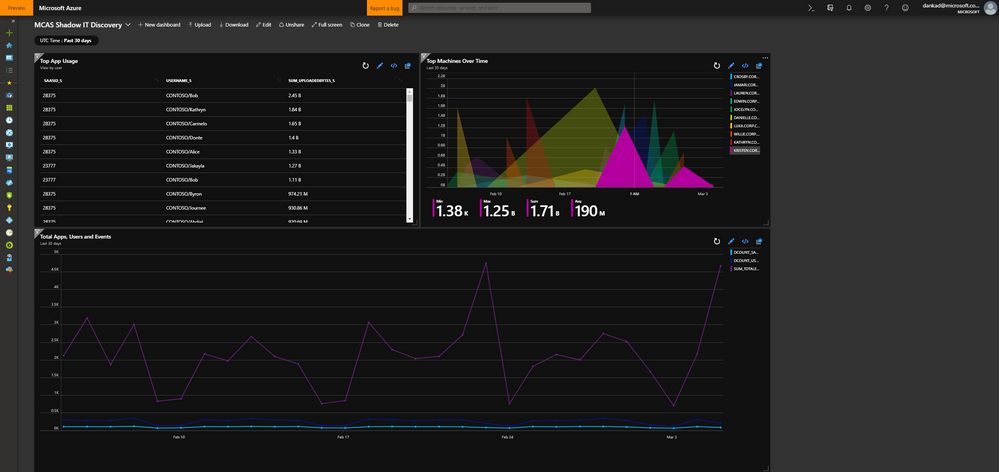
Bring your own data
Our Cloud Discovery data collects a specific set of data including target app URL, target app IP, username, uploaded bytes and more. But we’ve heard from many of our customers that they would like to add additional data points from other log sources and correlate the data directly. Examples include AAD attributes like department and region, to allow for a deeper user-based investigation. Through the new integration with Azure Sentinel, these datasets can now also be exported to Power BI, where organizations can add their own data sets and correlate it with the data collected by MCAS. Allowing you to run very specific queries against the correlated data sets and for e.g. look for high traffic users from a specific department.
Customized reporting
While Microsoft Cloud App Security natively offers a variety of built-in reporting options, including an executive report that summarizes the Cloud Discovery findings, the new integration with Power BI also enables organizations to create powerful, custom Power BI dashboards.
As described in the section above, it enables organizations to bring their own data and create custom queries. These custom data sets can then be used to create visually rich reports, providing flexibility and powerful reporting options to organizations via natively integrated products and simple workflows. The image below shows an exemplary dashboard that brings together Microsoft Cloud App Security Cloud Discovery data, custom data that was correlated via Azure Sentinel and a custom reporting dashboard that allows users to easily drill down into each of the sections.
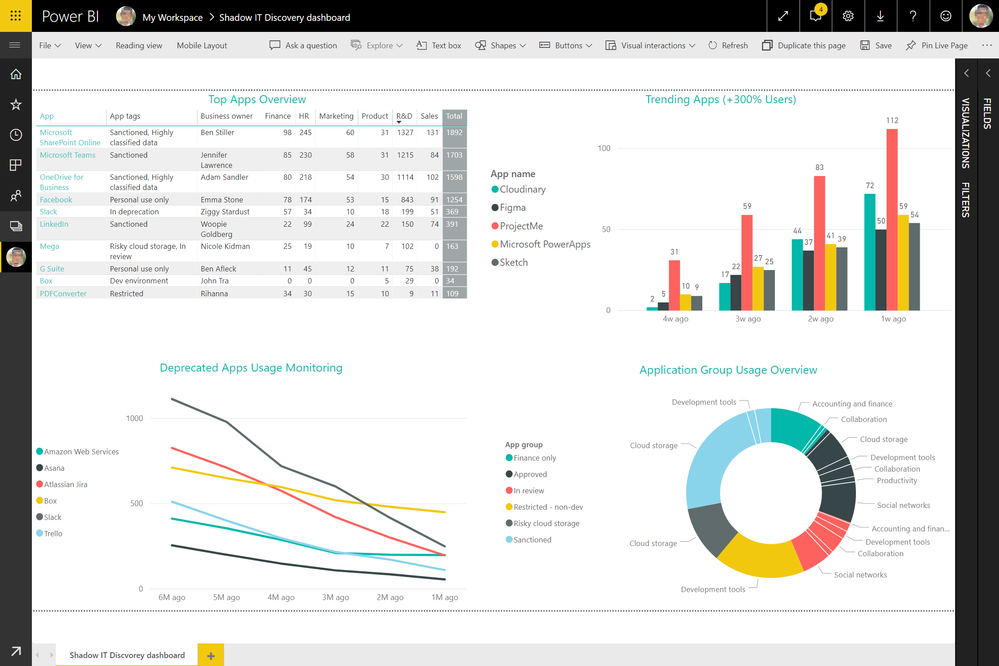
WDATP integration is now GA
Last year we announced a new integration with Windows Defender Advanced Threat Protection (WDATP), that enhances the Discovery of Shadow IT in your organization, and extends it beyond the corporate network.
Enabled with a single click, we are excited to announce that this unique integration is now generally available.
Protecting any cloud app
The key to a successful CASB solution is that it can help protect any of the cloud applications organizations use in their environment, as multi-cloud strategies are becoming the new normal. We continue to add new applications to our MCAS portfolio and are excited to announce a new API connector, as well as several new featured apps for our real-time controls via Conditional Access App Control.
Cisco Webex Connector
We’ve added a brand new connector for Cisco Webex and now provide the same powerful controls that we support for our other connected apps, giving organizations even more flexibility for their cloud app environments.
More featured apps for monitoring and controlling user actions in real-time
Conditional Access App Control became generally available (GA) last summer and allows you to control and limit access to your cloud apps and the files and data that you store within them. It utilizes a reverse proxy architecture and is uniquely integrated with Azure AD Conditional Access, to provide powerful real-time visibility and controls.
We recognize the importance of business applications organizations, and the sensitive nature of content within these apps. To help maintain productivity while handling sensitive customer data, we’ve added real-time monitoring and control for Dynamics 365. In addition, we are constantly focused on securing your most sensitive resources, and therefore continue to feature more apps, most recently the Azure Portal and LinkedIn Learning. The full list of currently featured applications can be found here.
Any app support - Become a design partner in our latest private preview!
While our featured application list continues to grow, we are aware that each organization is unique and may leverage SaaS apps not on this list, as well as custom applications, both on-premise and in the cloud. Therefore, we are extremely excited to let you know about a new private preview we are kicking off, enabling you to onboard any web application to Conditional Access App Control, to provide real-time monitoring and control. During the preview phase, space is extremely limited. To discuss your eligibility, please contact us at mcaspreview@microsoft.com
Today we have discussed a wide range of powerful announcements, as we continue to innovate in the CASB space. In the coming weeks we will discuss many of these topics in even greater detail as they are released into the product, and will provide specific use-cases, of which many are directly inspired by working closely with our customers.
.
More info and feedback
Learn more about Microsoft Cloud App Security here.
Haven’t tried Microsoft Cloud App Security yet? Start a free trial today and kick off your deployment with our detailed technical documentation.
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
1Microsoft Intelligence Report Volume 24 (https://info.microsoft.com/ww-landing-M365-SIR-v24-Report-eBook.html?lcid=en-us)