Microsoft Intune can integrate data from mobile threat defense (MTD) partners as an information source for device compliance policies and to evaluate Conditional Access rules based on device risk. By blocking compromised mobile devices from ability to access to corporate resources like Exchange and SharePoint, this information helps organizations protect the modern workplace against device based attacks. In the past, this capability required end users to enroll their devices with Intune for mobile device management (MDM).
Microsoft is excited to announce that device-risk based app protection integration with mobile threat defense vendors is now available to unenrolled devices, such as bring-your-own (BYO) device users or others where the device itself is not managed. We worked closely with our partners to create a seamless and intuitive experience for setup on an end user device.
This capability is initially rolling out with our partners Lookout for Work, Better Mobile and Zimperium. In future, we expect other partners to add support for this integration.
How does this benefit you as customers?
Digital transformation has enabled organizations to support a variety of device use cases, from providing company-owned devices to end users, to allowing work data on user-owned devices, to limiting the kind of apps users can have on devices used for work, and so on. While this creates opportunities for unprecedented flexibility and collaboration in the organizations, it also spreads the attack surface such that a malware or security threat on any one of the devices could compromise other devices or the entire network. Intune works with mobile threat defense partners to detect and evaluate acceptable device-risk status such as root detection, compromised apps, and network-based attacks before allowing access to the corporate network. Non-compliant devices are removed from the network until they are back in compliance.
This new capability we’re announcing here is a unique advantage to Intune customers that is not yet available with other EMMs. While other solutions require the device to be enrolled and managed for this security feature to work, Microsoft Intune extends the zero-trust security perimeter to all protected users, including both enrolled and unenrolled mobile devices running apps protected by Intune app protection policies.
Get started and learn more
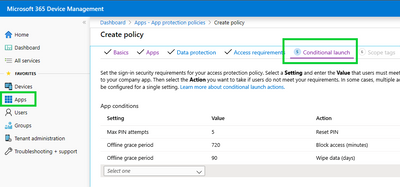
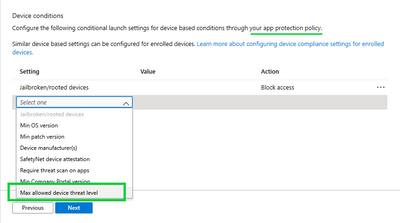
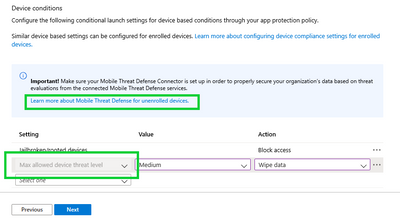
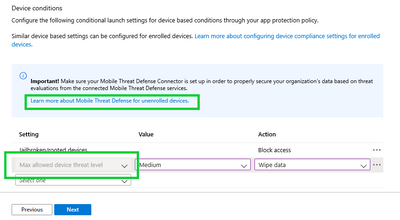
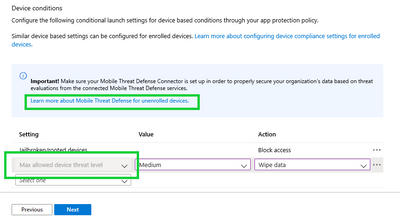
IT admins can find the new setting under the Conditional Launch section of their app protection policy for Android and iOS. Select the target the apps they wish to protect (either block access or selectively wipe) and create the device condition check for “Maximum allowed device threat level”.
Provide the action if the required threat level is not met and pick the Azure AD user groups on which this setting will be evaluated.
On Android, this feature will be available via the latest version of the Company Portal. On iOS, this feature will be made available as more apps adopt the Intune SDK for iOS with this functionality in place.
The refreshed interface of the Intune admin center provides helpful links to learn more about the feature from within the console. Visit the product documentation to learn more about Intune mobile threat defense on unenrolled devices.
Come see us at Microsoft Ignite
The Intune team will be at Microsoft Ignite doing a walkthrough of how to enable this capability as an IT admin, and what the experience on an end user device looks like for both Android and iOS. If you are attending, make sure to add this session to your schedule or come say hi at our Microsoft Showcase booth in The Hub. For those who cannot make it in person to Orlando, the on-demand recording will be available shortly after the session. Microsoft Ignite is happening from November 4–8, 2019 in Orlando, USA.
Next steps
Our engineering team has continually received feedback from customers during the process of building out this experience, and we are excited about this new capability and ease of use. We encourage you to share your feedback about the new features in comments below, and suggest new feature requests using User Voice.
For more information on how to deploy Microsoft Intune, add our detailed technical documentation as a browser favorite. Don’t have Microsoft Intune? Start a free trial or buy a subscription today!
If you have any other suggestions, questions, or comments, please visit us on our Tech Community page

(This blog is co-authored with Aasawari Navathe, Program Manager, Microsoft 365)