Many high-security organizations offer secure passwordless access to corporate data using smart cards. The end user does not have their username and password. Employees and contractors use physical smart card readers to authenticate themselves for secure access to desktops and laptops. Smart cards provide seamless and secure authentication to apps, websites, Wi-Fi, and VPN as well as enable the use of S/MIME to sign and encrypt email. With mobile user productivity becoming commonplace in enterprises, many government and high security customers wonder how to embrace mobility while still maintaining a highly secure environment. When we think about a standard mobile device enrollment experience, the end user begins by entering their username and password which enrolls their device. Various policies, including certificates, are then pushed to the device without further user interaction.
Since smart card users don't have their passwords, how do they authenticate if they can't plug their smart card into their phone?
To address this high security use case while enabling the use of mobile devices, the National Institute of Standards and Technology (NIST) created guidelines for derived Personal Identity Verification (PIV) credentials as part of Special Publication (SP) 800-157. The document provides technical details and guidelines on how customers using physical smart cards can obtain a certificate that can be used on mobile devices for authentication and S/MIME signing and encryption.
Microsoft Intune is excited to announce support for derived credentials on iOS devices.
Microsoft Intune support for derived credentials
Microsoft has integrated with partners including Entrust Datacard, Intercede, and DISA Purebred for the initial release of derived credentials in support of NIST 800-157 requirements. This is available immediately on iOS devices. In the future, we will add support for Android Enterprise fully managed devices, Windows 10, and integration with other derived credential partners.
So how do smart card users join the secure passwordless revolution from their mobile phones if they cannot plug-in their smart card into their phone for authentication? Well, they authenticate using the smart card reader on a trusted device which links the authentication with their mobile device. A digital certificate is then issued to the mobile device. In order to make the user experience smooth for end users, the derived credential enrollment flow is built into the Intune Company Portal app, which is the app used to enroll the device with Intune. As we will see in the next section, users will be prompted shortly after enrollment to retrieve their derived credential and will be guided through the process.
Mobile device enrollment flow with derived credentials
Let's walk through the end user experience on day zero, where a user wants to enroll an iOS device into Intune management to get access to company resources, such as Office 365 apps on mobile. The end users authenticate twice using their smart card from a smart card enabled device: once to enroll the mobile device with Intune and once more with the derived credential issuer’s identity system. After successfully completing both steps, a digital certificate is issued to the mobile device:
- On a mobile device, the end user downloads and installs the Company Portal application from the public app store.
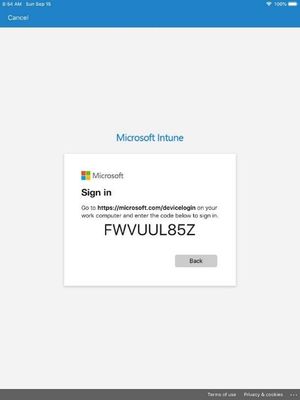
- As the user reaches the sign in screen, they choose Sign in from another device since they don't have their password.
- On a smart card enabled device, such as a Windows PC, the user is directed to a sign-in website https://microsoft.com/devicelogin to complete their authentication request using the code that is displayed on their mobile device.
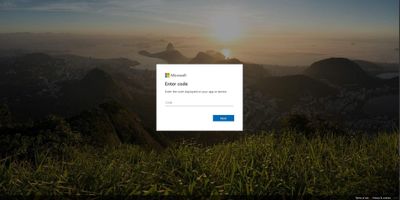
- The user enters this code into the https://microsoft.com/devicelogin site on their Windows PC and authenticates with their smart card, which completes the authentication request for the Company Portal login. The user then completes the rest of Intune enrollment workflow on the mobile device.
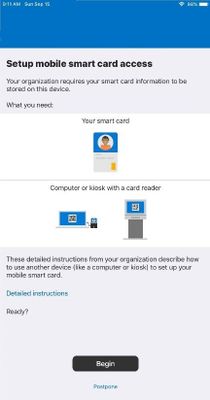
- After Intune enrollment, an app notification for Company Portal informs the user that they need to go through the enrollment process to get a mobile smart credential (their derived credential). Alternatively, email notifications can be used as well.
- After clicking on the notification, the user is taken to the derived credential enrollment flow within the Company Portal and follows the process to get the certificate from the derived credential provider onto the device.
- This part of the process varies depending on the certificate provider, but generally involves using a physical smart card on a trusted PC to authenticate with the provider's identity system and linking the authentication request on mobile device. Depending on the provider, the user may have to scan a QR code on the mobile device.
- Once the process is complete and certificates are received, the mobile device can be used for authentication, signing, and encryption, as defined by the policies configured by the administrator.
S/MIME signing and encryption with Microsoft Outlook
In addition to derived credentials for authentication, a significant number of government and high security customers also use S/MIME to sign and encrypt email. To further improve email security, Outlook recently began rolling out S/MIME support on iOS. Soon, you will be able to use derived credentials delivered via Intune’s integration with our partners for S/MIME signing and encryption with Outlook.
Microsoft Outlook for iOS and Android provides a fantastic end user experience, combining mail, calendar, and contacts into a single app. Additionally, Outlook contains enterprise protection capabilities against accidental data leakage using Intune app protection policies, and APP also ensures sensitive corporate data is completely wiped from the device when a user leaves the organization.
Next steps
We’re excited to enable Microsoft administrators to adopt the secure passwordless future across all their devices with the industry’s leading manageability and security platform. With support for derived credentials, high-security Microsoft Intune customers can deliver a consistent experience to smart card users on not only Windows devices, but mobile devices as well. To get started, check out the derived credentials documentation for instructions to integrate with our partners, including Entrust Datacard, Intercede, and DISA Purebred.
More info and feedback
For more information on how to deploy Microsoft Intune, add our detailed technical documentation as a favorite. Don’t have Microsoft Intune? Start a free trial or buy a subscription today!
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
Follow @MSIntune on Twitter
(This article is co-authored with Lance Crandall, Principal Program Manager, and Tiffany Silverstein, Program Manager 2)