This post is authored by Itay Argoety, Product Manager, Azure ATP
Enterprise security operations (SecOps) often have limited resources and staff, and security analysts face evolving, more sophisticated attack methods. Many of the newest tools and vulnerabilities can often go undetected without the right tools.
Today, Microsoft is expanding the preview of the Unified SecOps Experience which includes the new Investigation Priority.
The new Investigation Priority uses information from Azure ATP, Microsoft Cloud App Security (MCAS), and Azure AD Identity Protection to add powerful User and Entity Behavioral Analytics (UEBA) capabilities into Microsoft Threat Protection, to better help organizations in attack detection and incident investigation.
UEBA for Azure ATP, MCAS, and Azure AD Identity Protection
Identifying the riskiest users in your organization and their potential impact has remained a labor-intensive process - until now.
Instead of trying to connect the dots between alerts in the queue and active hunting, our user and behavior analytics highlights which users in your organization pose the biggest potential risk.
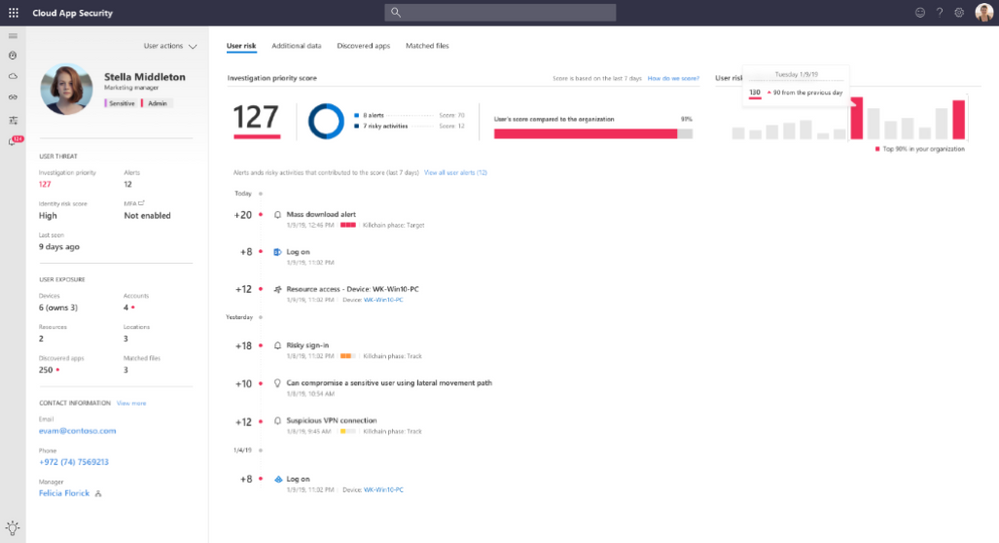
The Investigation Priority engine pulls signals and data from Azure ATP, Microsoft Cloud App Security as well as Azure AD Identity Protection. Activities and events from these solutions are scored based on their abnormality and aggregated into users’ Investigation Priority score. This allows SecOps analysts to identify the users posing the most risk to the organization, should they be compromised.
By identifying and surfacing the top users to investigate within your organization, this unified platform removes the guess work for security analysts by showing the greatest potential asset and business risks exposed by these suspicious users and their actions, in a single pane of glass.
Calculating the Investigation Priority
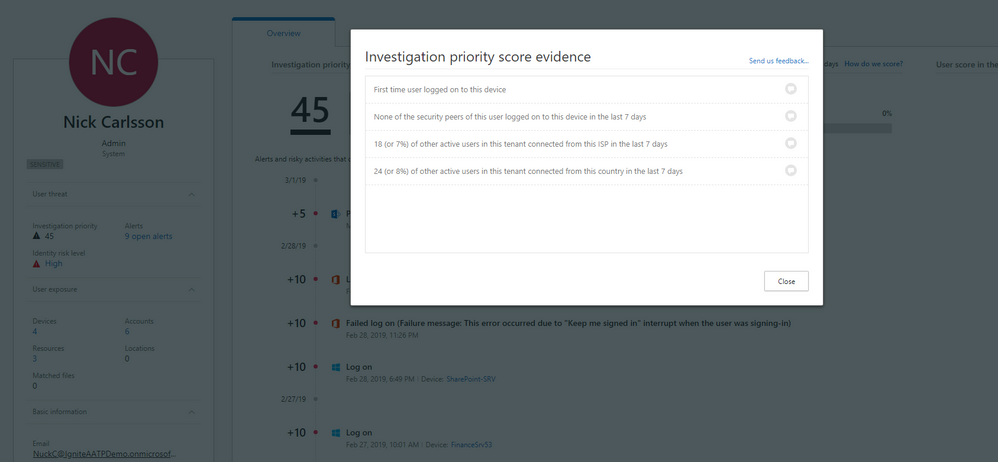
Analytics are used to build the standard profile and behaviors of users and entities across both time and peer group horizons, while activity that is anomalous to your standard baselines is evaluated and scored. Once scoring is completed, we apply Microsoft patent-pending machine learning and proprietary dynamic peer calculations, to offer the fastest possible Time-to-Remediate (TTR) workflow.
The Investigation Priority Score provides you the ability to detect both malicious insiders and external attackers moving laterally in your organizations, without having to rely on standard deterministic detections.
Investigation Priority Score:
Assessing the investigation urgency of each specific user, the Investigation Priority Score is based on security alerts, abnormal activities, and potential business and asset impact related to each user.
Every Azure AD user has a dynamic Investigation Priority Score, that is constantly updated based on recent behavior and impact, built from data evaluated from Azure ATP, Microsoft Cloud App Security as well as Azure AD Identity Protection. Your SecOps team can now immediately understand the real top user threats by Investigation Priority Score, and then directly verify their business impact and investigate all related activities – no matter whether they are compromised, exfiltrating data or acting as insider threats.
Alerts scoring:
Understand the potential impact of a specific alert on each user. Alert scoring is based on severity, user impact, alert popularity across users, and all entities in the organization.
Activity scoring:
Determine the probability of a specific user performing a specific activity, based on behavioral learning of the user and their peers. Activities identified as the most abnormal receive the highest scores.
User impact (blast radius):
Gauge the potential damage each specific user can cause to your business. The user impact analysis takes a holistic organizational user approach, assessing user role, group membership, privileges, hierarchy at the organization, access to sensitive resources (high value assets), and the ability to access sensitive information. This capability will be coming soon.
Azure Sentinel & Investigation Priority:
With the newly announced Microsoft Azure Sentinel, the Investigation Priority Score will also be based on specific data types onboarded into your Azure Sentinel workspace. Custom alerts created in Azure sentinel will be scored and will impact the Investigation Priority of users.
Used together, the solution offers a unified user investigation priority for Azure AD users across Azure Sentinel, as well as the other services in Microsoft Threat Protection.
Participate in the evolution of the Unified SecOps Experience
If you’re one of the many enterprise customers already using Azure ATP, MCAS, or Azure AD Identity Protection (or a combination of these) and want to experience this new functionality, join our expanding preview program.
Get Started Today
If you are just starting your journey, begin trials of the Microsoft Threat Protection services today to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace:
- Windows Defender ATP trial
- Office 365 E5 trial
- Enterprise Mobility Suite (EMS) E5 trial
- Azure Security Center trial